Integration with Let’s Encrypt
Introduction
Let’s Encrypt is a free certification authority that provides free X.509 certificated for TLS encryption. An automated process enables to facilitate the creation, verification, setup, and renewal of SSL certificates for protected websites.
The official website. Let's Encrypt integration page on ispmanager website
Let’s Encrypt provides a number of limits:
- You can order only 50 certificates per week (TLD, including its subdomains);
- Let’s Encrypt certificate validity period is 3 months (every 3 months ispmanager will reissue Let’s Encrypt certificates);
- All alternative names should be subdomains of the certificate domain.
More information about additional limits can be found here.
This module is available in ispmanager 5.131 and later.
In order to install a plug-in as root, navigate to Integration → Modules.
After you have installed Let’s Encrypt in ispmanager, you can obtain a self-updated SSL-certificate for your domain. Be sure to create a user with the configured web-domain and valid domain name available to world-wide DNS.
Once the installation is completed, in the WWW → SSL-certificates module the user will see two new buttons — Let's Encrypt and Let’s Encrypt Log. Clicking the first button will start the process of the certificate issue.
The second function will be activated, if you already have the Let's Encrypt certificate in the list of SSL-certificates, and will redirect you to the Event log.
Before generating a certificate make sure that the Let's Encrypt function is enabled:
- In the section "Access to functions": Settings → Access to functions → select a user group → Permissions → SSL certificates → Let's Encrypt → Enable.
- In the user permissions configuration form: Accounts → Users → select a user → Permissions → SSL certificates → Let's Encrypt → Enable.
Add a certificate
There are two ways to obtain a Let's Encrypt certificate:
- Navigate to WWW → SSL-certificates. Click the Let's Encrypt button, and fill out the form.
- On the WWW-domain creation form, select the Secure connection (SSL). Let's Encrypt certificate option will be added to the creation form. Specify the required parameters. Next, you will be redirected to the Let's Encrypt certificate creation form.
Certificate update
Every day at 1:30 a.m the system checks what certificates should be updated. The update procedure starts 7 (or fewer) days before the certificate expiration date.
You can also start the update process manually with the letsencrypt.check.update function. Call the function via the mgrctl utility with the following parameters:
/usr/local/mgr5/sbin/mgrctl -m ispmgr letsencrypt.check.update force_update=yes cert_name=%cert name% user_name=%user name%When updating the certificate with DNS-verification, new TXT-records will be generated. If the external DNS-server is used, the records won't be added automatically, and the certificate won't be updated.
Certificate issue procedure
First, a self-signed certificate with the specified parameters is created, then, once a minute, an attempt is made to obtain a certificate. You can set the maximum number of certificate requests that the control panel will send simultaneously. To do this, change the LetsencryptProcessCount parameter in the ispmanager configuration file. The default value for this parameter is 1.
If errors occur, they are logged. Retrying to receive is performed every minute. Requests for new certificates take precedence over retrying old ones.
You can start the letsencrypt.periodic command via the mgrctl utility.
If the certificate cannot be obtained within 24 hours, the corresponding notification will be created for the user and administrators. No more attempts will be made.
If the certificate is issued successfully, the self-signed certificate is changed into Let's Encrypt. The user and administrators receive the notification that the certificate has been issued.
Order of requests:
- Account creation
- Authentication
- Request for domain ownership (in order to verify domain ownership, a new token is added. This is a file with data that were received after authentication. The global alias .well-known/acme-challenge/ on the server leads to the directory /usr/local/mgr5/www/letsencrypt. All verification tokens will be created there.
- Waiting for successful validation
- Certificate issue
DNS validation
Let's Encrypt supports DNS-based validation that requires specific TXT records to be inserted into the DNS zone for a domain. Select the DNS validation checkbox when you order a new SSL-certificate.
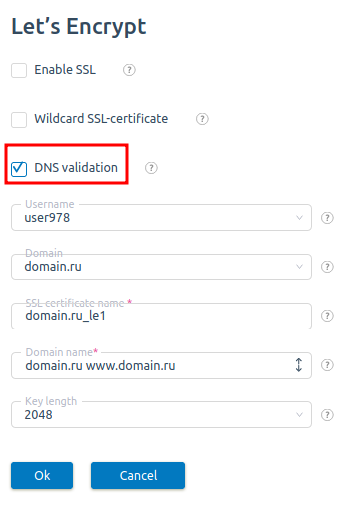
TXT-records will be automatically added in Domains → Domain names → Records.
If domain validation processes cannot be completed successfully for 24 hours since you ordered a certificate, the system will stop trying to issue the certificate.
Mail domains
Let's Encrypt can be issued for mail domains. Navigate to Mail domains → click Add or Edit → select New Let's Encrypt. The certificate will be also issued for aliases mail.domain.name, smtp.domain.name, pop.domain.name. If the web-domain with the same name is not created in the control panel, the verification procedure will run via DNS.
Wildcard certificates
Starting from version 5.147.0 ispmanager supports wildcard SSL certificates. To receive a Wildcard SSL-certificate check the Wildcard box on the order form.
Non-standard situations
Sometimes it may happen that a web-domain is resolved to several cluster nodes. If one of the cluster nodes doesn't have a web-role it cannot pass the HTTP verification. How to solve the issue:
- Pass the DNS verification.
- Just wait. After several failures, the ACME server will find the right address for the HTTP verification.
Logs
The log file is located in /usr/local/mgr5/var/letsencrypt.log.
The default logging level is not enough for receiving all the information an administrator may need to solve possible issues. Complete the following steps:
- Go to Settings → Logging settings
- Press Ctrl and select ssl, rpc, core_modules.
- Click on Maximum.